Due Diligence
This document provides information on a range of topics that may need to be reviewed by stakeholders as part of the process of purchasing a Gorilla subscription or getting approval from your Internal Review Board or Ethics Committee. If you have further questions, please don't hesitate to contact us by email (info@gorilla.sc).
If you want to read more about Gorilla Product and its Technical Side visit our Gorilla FAQ page.
Company Information
Gorilla is made, owned and sold by Cauldron Science Ltd (Cauldron).
Cauldron is incorporated in England and Wales under company number 07071678. Our VAT number is GB996693829. We are a micro-SME.
We are registered with the ICO under
registration number ZA245277.
Our registered office is: 2 Old Bath Road, Newbury, Berks, RG14 1QL
Our business address is: St John's Innovation Centre, Cowley Road, Cambridge, CB4 0WS.
Terms and Conditions
Please find below, links to our Terms and Conditions documentation:
Where will my data be stored?
Gorilla is hosted on Microsoft Azure within the EU (Republic of Ireland) which is compliant with ISO/IEC 27001:2005. Our backups are located in the Netherlands.
We also use a range of other suppliers. We have a signed Data Processing Agreement (DPA) with each of them, and we ensure that all of our providers have excellent security and privacy in place and are fully GDPR compliant.
We use a limited subset of suppliers to process participant data.
We also have a full list of the suppliers we use to process researcher/user data.
Who owns my participant data?
You are the owner (Data Controller) of any data you collect (participant data from any experiment where your account is the project owner). We will never view or use your participant data, unless we receive your explicit permission (i.e. if you have a support question about your data).
Your data is downloadable from your experiment as a spreadsheet, and once you download it you have complete control over how it is stored and used.
Can I delete my data/account?
You can choose to delete participant data you own (participant data from any experiment where your account is the project owner) at any time.
You can also choose to delete your account at any time. You can find steps to delete your Gorilla account in our Gorilla FAQ guide.
Deleted data is cleared from our backups within 14 days.
You cannot delete data or accounts from other users, even if you are their subscription manager or university supervisor. Accounts are owned by the individual user, not by the university or company. You can remove a user from your subscription and reclaim their unused participant tokens, see our subscription administrators guide for more information.
Does Gorilla have accessibility features?
Cauldron Science Ltd understands the importance of ensuring that its product is usable by all, including people with disabilities.
For a closer look, view our accessibility roadmap.
Internal Review Boards / Ethics
We're often asked to provide draft text for an Internal Review Board (IRB) or Ethics Committee. Below you will find information about Gorilla that could be useful for your application.
Gorilla
We will use Gorilla (www.gorilla.sc) to collect data for our study.
Gorilla is a cloud software platform specifically for the behavioural sciences. Here are some key facts about their data security:
- Cyber Essentials Plus: Certificate of Assurance - a6d4ef89-cb2b-4c47-80a6-863ee4d8c883
- Hosting: Gorilla is hosted on Microsoft Azure within the EU (Republic of Ireland) which is compliant with ISO/IEC 27001:2005
- Traffic Encryption: All traffic to and from Gorilla is encrypted (TLS/SSL)
- Database Encryption: The database is encrypted using industry-standard cryptography
- Data Ownership: The experiment owner owns the research data that has been collected using Gorilla and has complete control over it. Experiment data can be deleted by the experiment owner and will be removed from our backups within 14 days.
- Data Protection: Gorilla is fully compliant with data protection legislation
- BPS: Gorilla is fully compliant with BPS guidelines.
- GDPR: Gorilla is fully compliant with GDPR.
- IP Address: Gorilla does not collect or store IP addresses by default.
Recruitment
- Data Collection: Participants will take part via a desktop computer, laptop, tablet or phone from [anywhere in the world]
- Consent: Participants will give consent within Gorilla [see supporting documentation]. Participant can opt to not give consent.
- Recruitment Policy:
- We will use an anonymous recruitment policy in Gorilla. Consequently, once data is collected it cannot be deleted as it cannot be identified. Participants can still withdraw from the experiment at any time by closing their browser.
or
- We will use a recruitment policy in Gorilla that provides participants with a unique and non-identifiable key [ABC123456] that allows them to withdraw their data after completing the experiment.
or
- We need to collect data from participants over several days and therefore want Gorilla to email participants to remind them to take part.
Consequently participant email addresses will be uploaded to Gorilla.
- To ensure complete confidentiality and data security, participants are first given a Public ID (ABC123456) which they can use to log in with.
- Performance data is stored against a Private ID (X1Y2Z345).
- The relationship between the email address and Public ID is stored separately from performance data.
- The relationship between the Public ID and Private ID is stored separately from performance data.
Anonymity and Ethics
In compliance with BPS (The British Psychological Society) requirements, identifying data, demographic information and performance data are all stored separately. They are downloaded separately from the Data tab and joined together outside Gorilla using the Private IDs provided.
Our database architecture supports double-blind studies; you can join demographic data with performance data while remaining blinded.
Participant Data collected using Gorilla is anonymous by default. The only exceptions to this are (1) when using email based recruitment policies as Gorilla requires the participants email address to send them emails, (2) experiments in which the researcher elects to use personally identifying participant IDs and (3) the researcher collects personally identifying data as part of their study. In all cases, the participant would have given their consent.
Data files from Gorilla provide a Public and Private participant ID. The Public ID is visible on the Participants tab so you can use this ID to delete participant data, for example if they choose to withdraw. It may also be an external ID, for example if participants come from Prolific this will show their Prolific ID (but you won't be able to see their actual data alongside this). The Private ID is randomly generated by Gorilla and stored separately from the Public ID by default. When you download your data, it's the Private ID that you'll see in the dataset and not the Public ID, which keeps the data anonymous. However, if for any reason you need to match the participant's identity to the data you can choose to connect the two pieces of information yourself by unblinding the data, but this has to be deliberately done by the researcher. The key distinction is that the Public ID enables you to keep track of the participant, but not their data, and the Private ID allows you to keep track of their data but not the participant. If you want to keep track of the participant and their data - you can then choose to unblind the data when downloading the file.
For the avoidance of doubt, IDs from 3rd party recruitment services (e.g. Prolific) are anonymous; we cannot link such an ID and the associated participant data back to an individual. Unless you explicitly collect identifying data (e.g. names or email addresses), your data is most likely anonymous.
By default, data for each participant only becomes accessible when the participant completes an experiment, so if a participant withdraws from an experiment partway through you will not have access to their data. However, you can choose to manually include a participant who is partway through an experiment, which will give you access to their data. You can also choose to manually delete the data for any or all participants at any time.
Informed Consent
When getting consent from participants it may be prudent to get explicit consent for using Gorilla and our sub-processors. We suggest the following text:
How will my data be processed?
By taking part in this study you consent to the use of Gorilla and their subprocessors receiving your data. The Gorilla servers are located in the EU, with some ancillary services (emailing, error handling) provided by suppliers in the USA.
In order to have informed consent, you may want to provide more detail, such as:
- The data collected will be anonymised
or
- The study will collect your email address in order to send you login credentials or email reminders
or
- The study will use personally identifying IDs, so your data can be identified
HIPAA
HIPAA compliance is a critical consideration when conducting any research involving protected health information (PHI), even in anonymous online studies. Here are some key considerations for maintaining HIPAA compliance in such studies:
- Anonymization: Ensure that all personally identifiable information (PII) and PHI are fully anonymized before data analysis. This includes removing or encrypting direct identifiers such as names, addresses, social security numbers, etc., and also removing any indirect identifiers that could potentially lead to the identification of individuals.
- Data Security: Implement robust security measures to protect the confidentiality and integrity of the data. This may include encryption of data both in transit and at rest, secure storage protocols, access controls, and regular security audits.
- Gorilla Security meets stringent university requirements. You can read more in our Technical Safeguards section.
- Informed Consent: Obtain informed consent from participants before collecting any data. Clearly communicate the purpose of the study, how their data will be used, and any potential risks or benefits involved. Participants should understand that their participation is voluntary and that they have the right to withdraw at any time.
- Our Questionnaire Tool makes it easy to create a consent form. More guidance in our Informed Consent section.
- Data Storage: Store data securely on HIPAA-compliant servers or platforms. Ensure that only authorized personnel have access to the data and that access controls are strictly enforced.
- Gorilla is hosted on Microsoft Azure within the EU (Republic of Ireland) which is compliant with ISO/IEC 27001:2005
- For additional security, you can opt into 2FA on your account.
- The project owner has control over collaboration features and data access.
- Data Sharing: If sharing data with third parties, ensure that appropriate data use agreements are in place to protect the confidentiality of the data. Limit data sharing to only what is necessary for the purposes of the study, and ensure that any third parties involved are also HIPAA-compliant.
- Retention and Disposal: Establish policies for the retention and disposal of research data in accordance with HIPAA guidelines. Data should be retained only for as long as necessary and securely disposed of when no longer needed.
- Gorilla affords researchers full control over their data retention and disposal workflow.
- Training and Education: Ensure that all individuals involved in the research study, including researchers, staff, and collaborators, receive training on HIPAA regulations and their responsibilities for maintaining compliance.
- This responsibility falls with the researcher and research team.
By following these guidelines, researchers can conduct anonymous online research studies while still ensuring compliance with HIPAA regulations and protecting the privacy and security of participants' health information.
Technical Attrition
Technical attrition due to any element between the participant's device and our servers is a reality of internet research, and we want to give you the information you need to make an informed decision.
- Short interruption: Some events will be so short that it will not affect your participants. The participant's computer will have stored a few trials ahead, so it’s possible that the connection is back up again before the participant needs more information. Gorilla stores participant data locally and will re-transmit any failed uploads.
- Longer interruption: Some events will be long enough that participants notice. It may still be sufficiently short that the participant has to refresh their browser, and in that case it might simply be a question of excluding a trial with a long reaction time or inter trial interval. In this situation, the event would have an impact similar to your participant being momentarily distracted.
- Critical interruption: Some events (e.g. a server issue or participant connection issue) will be long enough that participants cannot continue at that time. Depending on the recruitment policy and experiment, it might be that they can continue later. On the other hand, it might be that for experimental reasons, you can’t use their data.
The impact of technical attrition on your experiment will depend on your recruitment method and your target participants.
- If you are crowdsourcing participants for free - then just ignore this risk.
- If you are using a recruitment service, then you can mitigate the risk by releasing your study in batches. Generally this isn't necessary - participant pools are so big and the risk is so small that it makes more sense to tolerate the attrition.
- However, if you are recruiting from a small population (e.g. green-eyed bilinguals), then you may want to recruit in smaller batches.
On our side – as long as you haven’t included participants at the start node – no Gorilla fees would be due. If you are paying participants through a participant recruitment service, you may need to check their policy. Microsoft Azure guarantees that our servers will be working 99.95% of the time, and generally performs far above this threshold.
Overview
Gorilla is built to support the existing BPS (The British Psychological Society) and NIHR (National Institute for Health Research) standards which have strict codes of practice to adhere to, in addition to the legislative requirements of the GDPR and DPA2018.
To fulfil our Art 28 legal requirements as a Data Processor, we offer a Data Processing Agreement to our customers.
Data controllers accept our list of suppliers as part of our terms and conditions. If and when we engage additional sub-processors, the Data Controller is informed.
The Data Controller shall be entitled to object to any such change, provided that the Data Processsor shall not be liable to the Data Controller for any failure to provide any element of Gorilla as a result of such objection.
2021 Brexit Update:
The EU has granted temporary ‘adequacy’ to the UK in relation to its personal data regime until at least 30 April (and potentially 30 June) in order to ensure that personal data can continue to travel from the EU to the UK and vice-versa as it did prior to Brexit.
In parallel to this, we have put in place arrangements to apply if the UK is not deemed ‘adequate’ and is treated as a third country by the EU. Those arrangements comprise the appointment of an EU representative and making available a mechanism pursuant to which you can enter into the EU Standard Contractual Clauses with us.
As a result and regardless of the outcome of the current EU/UK negotiations, EU institutions are able to continue to do business with us in a GDPR-compliant way.
Processing of Data
With regard to the personal data processed in the Gorilla System, we are a Data Processor and the customer is the Data Controller. S10 of our Terms and Conditions clarifies this.
For data where the customer is the Data Controller and we are the Data Processor, we use a small subset of our suppliers. We only use services from these suppliers which are limited in scope and strictly necessary to provide our services.
2020 Update
Following the judgment in the Schrems II case issued by the European Court of Justice we have been following the advice and guidance of the ICO and EDPB so that we can implement recommendations swiftly. This is the current advice from the Information Commissioner's Office.
The suppliers this applies to are:
Microsoft Azure
- Web Hosting & Data Storage, hosted in EU (ROI and the Netherlands)
- Microsoft itself located in USA
- DPA signed with GDPR compliant SCCs
Participant Data collected using Gorilla is anonymous by default. The only exceptions to this are (1) when using email based recruitment policies as Gorilla requires the participants email address to send them emails, (2) experiments in which the researcher elects to use personally identifying participant IDs and (3) the researcher collects personally identifying data as part of their study. In all cases, the participant would have given their consent.
For the avoidance of doubt, IDs from 3rd party recruitment services (e.g. Prolific) are anonymous; we cannot link such an ID and the associated participant data back to an individual.
Rollbar
- Error handling
- Located in USA
- DPA signed with GDPR compliant SCCs
We use Rollbar for error reporting. In the event that something unexpected happens, we capture that event data and send it to Rollbar so that we can investigate. The error data that is sent to Rollbar depends on the nature of the error. Identifying data will only be sent to Rollbar if necessary to diagnose the error.
Sendgrid
- Email Delivery
- Located in USA
- DPA signed with GDPR compliant SCCs
We use Sendgrid for email delivery. This is used to send transactional email to researchers (account setup, password recovery) and also to send transactional emails to participants to enable them to take part in studies. Emails will only be sent to participants when researchers use email-based recruitment policies, or if a participant enters their email address to receive reminder emails as part of a longitudinal study. In both cases, the participant will have supplied their email address to the researcher and consented to take part in the experiment.
PostMark
- Email Delivery
- Located in USA
- DPA signed with GDPR compliant SCCs
We use PostMark for email delivery. This is used to send transactional email to researchers (account setup, password recovery) and also to send transactional emails to participants to enable them to take part in studies. Emails will only be sent to participants when researchers use email-based recruitment policies, or if a participant enters their email address to receive reminder emails as part of a longitudinal study. In both cases, the participant will have supplied their email address to the researcher and consented to take part in the experiment.
EU Representation
We have appointed Prighter as our EU Representative. You can contact them by submitting a request, or via their physical address:
9 Clare Street
Dublin 2 D02 HH30
Ireland
Please add the following subject to all correspondence: ID-14967537625
Retention and Access to Information
- Information accessible to Gorilla employees is managed in line with our retention and records management policies. These policies are owned and managed by the senior management team within Cauldron and detail the retention periods in place for the data within Cauldron.
- Access to Gorilla systems is strictly limited to those people who need to access them based on their role. If a person leaves the organisation, or changes their role, access is reviewed or revoked as appropriate.
- Data is created when a participant takes part in an experiment.
- Data is deleted when a researcher deletes the data.
- Deleted data is purged from our systems and not archived.
- No customer or personal data is transported between physical locations within Cauldron and the Data Controller is responsible for any data transported between locations within their organisation (e.g. if data is exported and printed)
Data Deletion
What happens to the data in a user’s account if they close their account?
- We delete their personal information (name, email etc).
- We retain a HASH of their email address, so if they want to restore their account, we would be able to recover it. A HASH is a one-directional encryption, so we can't use it to restore their account without them contacting us first.
- For any experiment where they are the owner: We move the project to a special 'orphaned' account in case a collaborator (or university) wants to claim ownership. We have no rights over User Content, even once they have closed their account.
- Researchers are able to delete individual participants from experiments via the UI.
- With this process, we've aimed to strike a balance between preserving potentially valuable research data while fulfilling expectations around privacy.
- Deleted data is automatically removed from our back-ups after 14 days.
How can a university keep access to data that they paid for?
- Researchers can collaborate with anyone else with a Gorilla account
- Technicians have the ability to access projects owned by members of their subscription with the owner's permission.
- Technicians could use this to ensure that a copy of data is downloaded and stored for posterity.
Third Party Suppliers
Follow the link to view a List of Suppliers.
- We perform an annual review of our suppliers to ensure that they continue to be compliant with our legal requirements. We also receive regular security bulletins from these suppliers.
- Our T&Cs, list of Suppliers and DPA are kept up to date with any material changes to the platform. When they change, users are required to reconfirm their acceptance of them.
- When you engage Gorilla as your Data Processor, we make you aware of the sub-processors involved in the processing of personal data via Clause 1.5 in the Data Processing Agreement.
- Agreements are in place which include detailed security requirements with any 3rd parties that are used to transfer business information between the organisation and external parties
- We have a process to formally review the information security controls of those third party suppliers who will have access to client data:
- Annual check of subcontractor status with respect to:
- GDPR compliance
- Lawful transfer mechanism for data outside of the EEA
- Review regular security and update bulletins from these suppliers
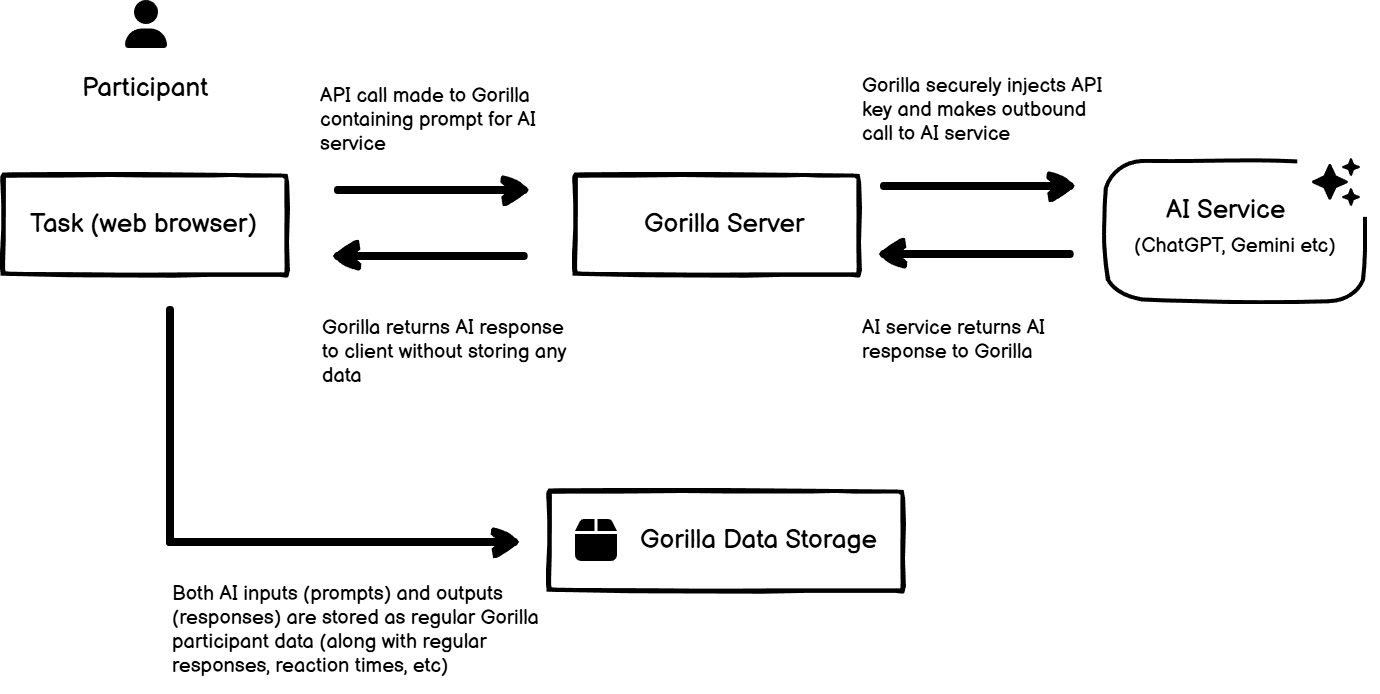
AI Integration
We have added the ability for researchers to integrate AI into their tasks. AI is only used in experiments when the researcher has explicitly added and configured it - Gorilla never sends any participant data to AI services internally. In order to secure the the researcher's API key, all calls to the AI service pass through the Gorilla server. The prompts and responses are then stored in the same way as regular Gorilla participant data (along with regular responses, reaction times, and so on). Gorilla doesn’t store any extra data along the way - everything that Gorilla has stored is in the data output. As per our Terms and Conditions, researchers are responsible for ensuring the legality, accuracy and compliance of any AI they choose to use.
As a data flow diagram:
Cookies
In addition to functional cookies (e.g. sessions and authentication), we use cookies for Google Analytics for analytics and Facebook for marketing attribution. These are only set if the user permits them first, using the banner that appears at the bottom of the screen when they first access the site:
These cookies are only set on the researcher side of Gorilla - we don't use marketing cookies on the participant-facing research.sc domain.
HR and InfoSec Policies
- All information security policy responsibilities are assigned to our CTO. The CTO is responsible for the content, updates and dissemination of all policies within Cauldron.
- All policies are peer reviewed by the CEO prior to publication.
- Staff are required to required to acknowledge receipt and understanding of information security policies, including updates.
- All employee contracts include standard NDA clauses relating to confidentiality of client and business information. Access to information is based on least-privilege and any breach of confidentiality is grounds for termination of contract.
- We have a robust Joiners, Movers and Leavers Process, which ensures that staff have access to all the information they need in order to fulfil their role, whilst also ensuring that no credentials remain for staff who move on, or for projects that are inactive.
- If a member of our team moves on to other employment, processes are in place to ensure that all devices and information are returned at the end of the last working day.
- Where Contractors are engaged by Cauldron, the same robust access management processes are used. This includes for privileged access. We only use established, reputable and industry leading subcontractors with appropriate contractual agreements.
Cyber Essentials Plus
We hold Cyber Essentials Plus certification: Certificate of Assurance - a6d4ef89-cb2b-4c47-80a6-863ee4d8c883. The registration can be viewed by entering ‘Cauldron Science Ltd’ into the search area.
Technical Safeguards
- Cyber Essentials Plus: Certificate of Assurance - a6d4ef89-cb2b-4c47-80a6-863ee4d8c883.
- Hosting: Gorilla is hosted on Microsoft Azure.
- Currently, all our instances are located in their North Europe region, which is within the EU (Republic of Ireland).
- Microsoft Azure is compliant with ISO/IEC 27001:2005.
- Personal Data and User Content will be uploaded from the Controller to the Processor SaaS environment where it stored with Azure's standard security protocols.
- Traffic Encryption: All traffic to and from Gorilla is encrypted (TLS/SSL)
- Database Encryption: The database is encrypted using industry-standard cryptography
- Penetration Testing Gorilla has been successfully penetration tested and no high-severity issues were found. A copy of the report is available on request.
- Ownership of Research Data: Users own their user content and the experiment owner owns the research data that has been collected using Gorilla
- Data Deletion: Participant research data can be fully deleted by the researcher. Responsiblity for deletion of participant data falls to the researcher including accidental deletion of participant data. Once data has been deleted it cannot be recovered. Researchers are able to delete all data for an experiment or data pertaining to an individual participant. When this action is taken, data will be removed immediately from the database, and cleared permanently from our automated backups after 14 days.
- Passwords: We use up-to-date cryptography techniques to handle passwords and user authentication. Passwords are 10 characters long and must contain a reasonable amount of entropy. They are stored as salted hashes in our database to prevent against rainbow table attacks. To prevent brute force attacks, after 3 failed login attempts, users have to wait for 10 seconds before they can try again.
- Two Factor Authentication: We offer Two Factor Authentication as a login option, to increase the level of security on your account. Further, for institutions that require it, you can force all users on your subscription to setup 2FA.
- Gorilla supports two forms of multi-factor authentication:
- SMS-based two-factor authentication (2FA), which can be enabled directly within Gorilla.
- Single Sign-On (SSO) via Microsoft Entra, which allows institutions to enforce their own MFA policies. (SSO is subject to additional fees.)
- These options let institutions choose the level and method of authentication that best fits their security requirements.
- GDPR: Gorilla is fully compliant with GDPR.
- IP Address: IP addresses are not provided in the data download.
- Risk Assessment: Our SaaS supplier is certified to ISO27001:2013 which is a risk-based certification. Evidence of risk assessment is a fundamental requirement of certification. We have access to Microsoft's Compliance Centre and are able to use their tooling to assess our risk
- The MS Azure 27001:2013 risk assessment covers end of life hardware and software and ensures that all systems are supported.
- Asset Management All hardware and software assets managed by Cauldron have been identified and documented in an asset register.
- Data Centre Security: All data relating to Client Projects is held in Microsoft Data Centres. As part of their ISO27001 certification, it is a requirement that suitable physical security is in place.
The DCs that are in scope of the certification can be found on the 27K certificate.
- Encryption (storage and transmission): User accounts are secure - passwords are stored using modern best-practice cryptography and reset keys are one-use-only
SSL is used as standard
- Service keys are held securely as Azure configuration settings and injected as environment variables (they never touch the codebase or developer machines)
- All SQL queries are parameterised properly
- All user input is sanitised and validated
- Patching and Vulnerability Management Cauldron-owned and managed devices all have auto-update (patching) and AV (Windows Defender) enabled and auto-updated. The OS is Windows 11 Pro in all cases. Change management processes are in place and any incidents following a change can be tracked back to the time and date so that remediation actions or change reversal can be performed. Event monitoring and vulnerability scanning are performed by Microsoft and any unusual activity investigated and remediated by the Cauldron CTO.
- Back-ups: Back-ups are taken by Microsoft in line with their Terms of Service.
- SDLC (Software Development Life Cycle) Software development lifecycle is as follows:
- Features are developed on local developer machines which do not connect to any production services.
- Builds are then deployed to a development server for testing, which is a completely standalone instance of Gorilla with its own separate infrastructure.
- Once tested, updates are deployed to production via a staging slot to allow for seamless service.
- Test data: All development is done using test data. When new features are released, they are done so as 'beta' releases to further confirm how they work with live data. No live data is used during the development of systems.
- Information Security Incident Management: All information security incidents are escalated to the relevant management as required. Our policy is to review the circumstances and take appropriate measures including termination of employment. While we do not operat or maintain critical systems ourselves, we have internal processes for managing incidents such as database overloads or CPU exhaustion to minimise disruption for our users. This is covered in Section 1.4.f of the Data Processing Agreement.
- Business Continuity: Microsoft Azure is certified to ISO22301.
HECVAT
To request access to our full HECVAT (Higher Education Community Vendor Assessment Toolkit), email procurement@gorilla.sc.
Accessibility Statement
For more information, have a look at our Accessibility Statement.
Roadmap
At Gorilla we understand the importance of ensuring our product is accessible to all users. We strive to have an inclusive offering through the following approaches:
- Consider accessibility when developing new and updated functionality
- Verify our product using guidance such as from the Web Content Accessibility Guidelines (WCAG), Section 508, and EN 301 549
- Respond appropriately when we become aware of deficiencies
Here is our current roadmap:
Researcher Side
- Improve accessibility of Support Docs and Academy ( complete)
- Improve the accessibility of the Gorilla marketing site ( complete)
- Add captioning to all support videos. In Progress.
Participant Side
Not yet scheduled in detail. We are currently working with our users and scientific advisors to design the right set of accessibility features to support their research, while ensuring that important methodological parameters are preserved.
For more information about this, please email info@gorilla.sc.
VPAT
We can provide a completed VPAT (Voluntary Product Accessibility Template) form for our webpages and the Gorilla application.
The VPAT is a free template that translates accessibility requirements and standards (e.g., in Section 508 and other legal frameworks) into actionable testing criteria for products and services. Users should test their products and services against each section of the VPAT and use the template to document results. Once completed, the VPAT® with documented testing results is referred to as an Accessibility Conformance Report (ACR) that details the accessible features of the tested product or service.
The Accessibility Conformance Report (ACR), based on a completed ITI VPAT®, is the leading global reporting format for assisting buyers and sellers in identifying information and communications technology (ICT) products and services with accessibility features. The VPAT includes the leading ICT accessibility standards: Section 508 (U.S.), EN 301 549 (EU), and W3C/WAI WCAG.
To request a completed VPAT, contact info@gorilla.sc.
Ongoing Development
We incorporate accessibility features as part of our development process, and continue to improve our existing tools as we develop them. If you have any problems accessing our site, please get in touch with our support team via our
support contact form.

